A vulnerabilty in all EON verisons has been detected except for the 5.3
Presentation
EON systems that boot in UEFI mode have a vulnerability. The vulnerability affects systems using Secure Boot, even if they are not using GRUB2. Almost all signed versions of GRUB2 are vulnerable, meaning virtually every Linux distribution is affected. In addition, GRUB2 supports other operating systems, kernels and hypervisors such as Xen. This vulnerability makes these devices susceptible to attackers such as the threat actors recently discovered using malicious UEFI bootloaders. The boot process is one of the most fundamentally important aspects of security for any device. It relies on a variety of firmware that controls how a device’s various components and peripherals are initialized and ultimately coordinates the loading of the operating system itself. In general, the earlier code is loaded, the more privileged it is.
If this process is compromised, attackers can control how the operating system is loaded and subvert all higher-layer security controls.
Red Hat Corp. has developped a program that can detect this vulnerability and possibly fix it. This is this one that allowed us to see wich EON systems were concerned.
According to our information, most affected machins are :
- VM under Hyper-V (because UEFI boot is set to default)
- Recent physical servers
Detection
If you want to be sure that your system is not affected by this vulnerability, you can run this script :
https://access.redhat.com/sites/default/files/cve-2020-10713–2020-08-01-1153.sh
To execute this program, you need to add execution acces and execute it. To do so, you will need to type those commands :
chmod +x cve-2020-10713–2020-08-01-1153.sh
./cve-2020-10713–2020-08-01-1153.sh
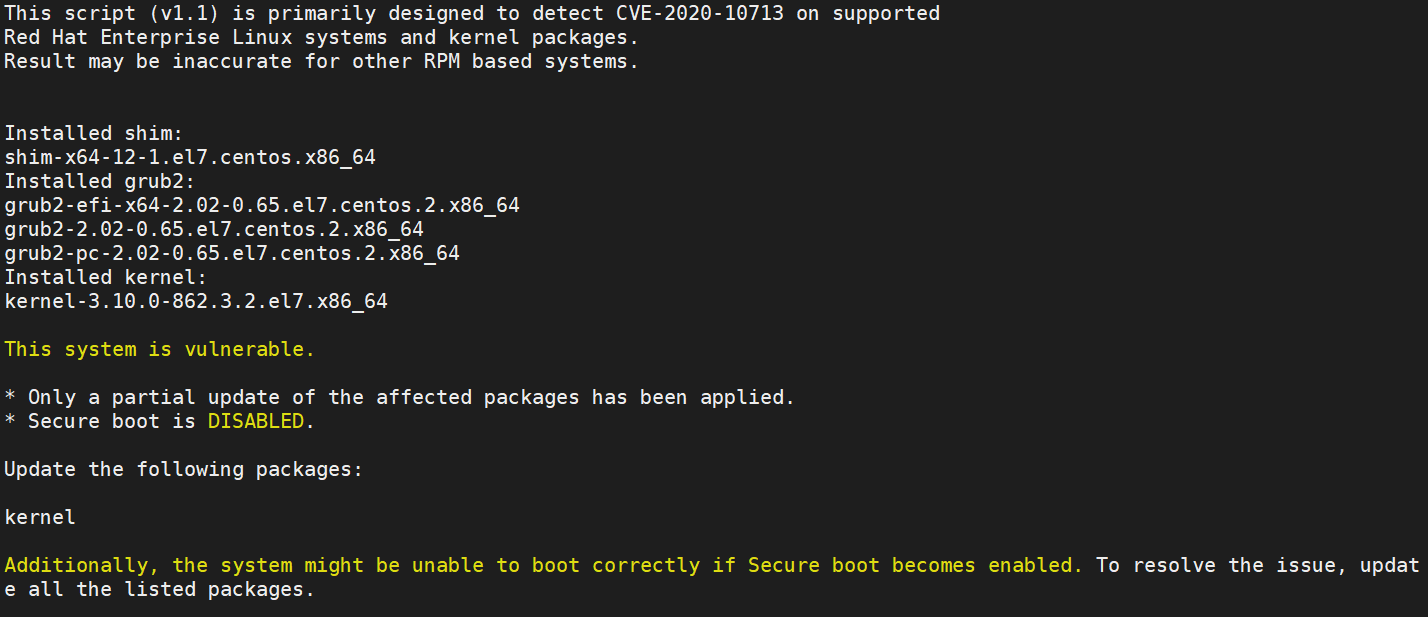
If your system is concerned by the vulnerability, you should have this kind of message :
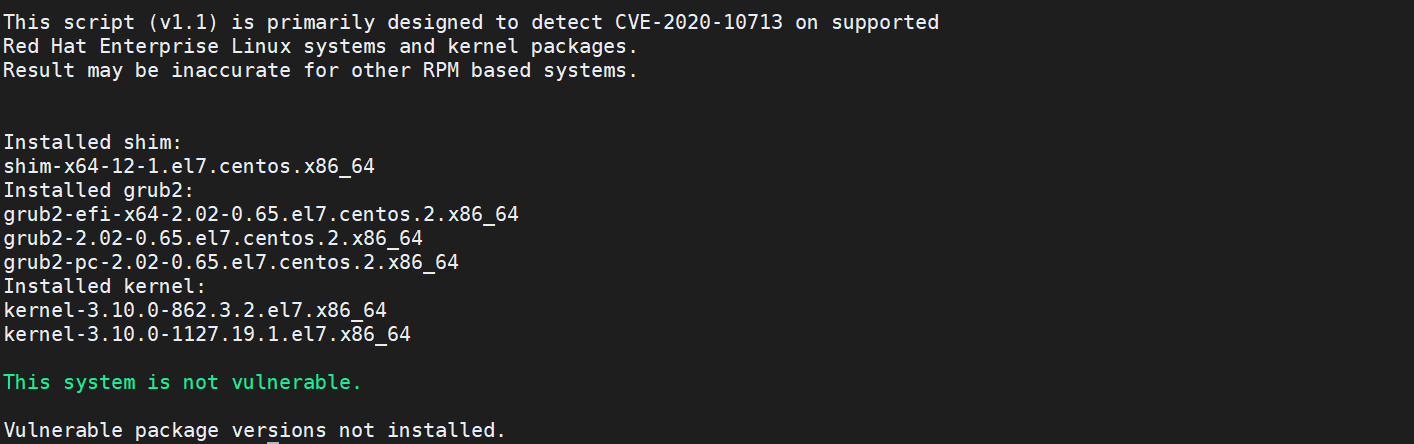
If not, you should have the following message :
Correction
- If your system is vulnerable and you got the same message in the Detection section, then you just have to update the Kernel packet. To do so, just execute the following command :
yum update -y kernel
After doing this, just verify that your system is no longer vulnerable by re-executing the program.
- If your system is vulnerable but the message you got is different from the Detection section, then just refer to this article : https://access.redhat.com/security/vulnerabilities/grub2bootloader
Sources
https://access.redhat.com/security/vulnerabilities/grub2bootloader https://www.futura-sciences.com/tech/actualites/cybersecurite-boothole-faille-redoutable-affecte-ordinateurs-equipes-windows-linux-82227/ https://eclypsium.com/2020/07/29/theres-a-hole-in-the-boot/